Last week, our Xinet interface E6 hit a major milestone - 15 Million page views! Since its launch 4 years ago, we've watched with awe as our users adopted, extended, evangelized and brought the best out of the NAPC product suite (and our development team). Click here for a free trial copy!

Across 6 continents (dang you, Antarctica), 137 countries, and all 24 time zones, People are working faster, smarter, and more efficiently, every hour and everyday. I've had hundreds of conversations with users, gotten ideas and feedback, and worked the agile process to get the best product to market swiftly. We started from scratch - an entirely new development team, an entirely new attitude, and one huge blank slate.
We knew speed was paramount. Feedback to user actions critical. A beautiful, easy to use interface a must have. Mobile friendly or stay at home. Always ready, well in advance of the latest Xinet version was a non-negotiable checklist item. Improving navigation across all interfaces and reducing clicks was also a flat out requirement.
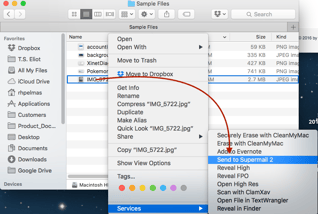
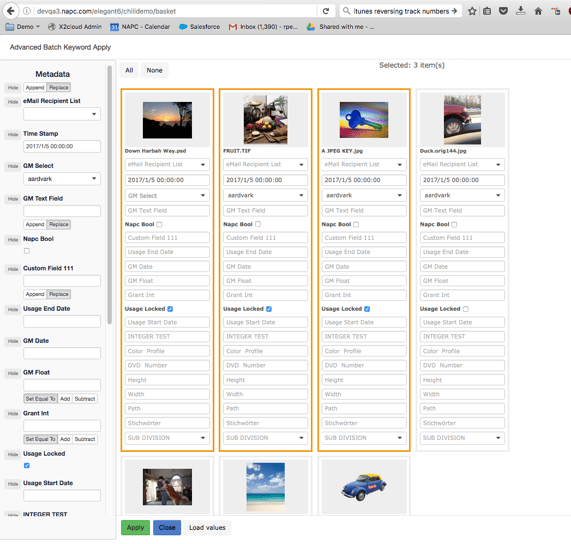
Thanks to agile methods and a fantastic team, it all got done! We released and started getting feedback, our development group became an even more manic whirl of ideas and creativity. We attacked metadata entry: creating a simple, intuitive, all-in-one single screen entry point. We added multiple ways to send Supermail - from the finder, and from our 'steal a link' feature. Our eyes are always focused on making production and sharing of assets easier.
Next we created beautiful new themes that are interactive and customizable; built out a screamingly fast and stable SSO with the IdP of your choice; did a complete rewrite of AFR to rigidly enforce DRM. The snowball was rolling, gathering size and momentum. Integrating site creation, login, and theming in one single screen and admin interface. Creating an API that will never change, allowing easy-peasy creation of Xinet plugins.
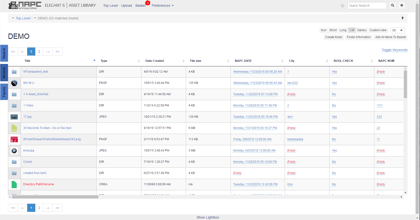
vFolders (dynamic collections of assets) eliminates the need to manually notify folks of new assets or new completed work. Alongside the automatic application of metadata, new things show up in a users Virtual folder. Xray (top level DAM search without logging in) is our latest feature. Find something, and grab that preview for your deck on the fly. Or login and get the hi-res version. Heck, open the asset directly in the finder from search results.
In sum, thanks for your love, care, and feedback. E6 allows Xinet users to see further and more accurately into their work and production solely because we stand on the shoulders of giants - the user community. Thank you!
To mark this milestone, we'd like to offer a free trial to the entire Xinet community. If you're looking for more from your Xinet interface, take E6 for a spin. Self installable, lives alongside any Xinet Portal install, it "just works". We'd love for you see what we've been up to, and maybe make your work lives a fair bit better.
Click here to D/L a copy of E6 and prepare to be blown away.








 Production Central seamlessly joins E6 with proofHQ® to deliver an intelligent, enterprise-level softproofing solution. Infinitely configurable, Production Central leverages your existing [and future] job structure(s) to automatically generate and manage proofHQ proofs and send email notifications.
Production Central seamlessly joins E6 with proofHQ® to deliver an intelligent, enterprise-level softproofing solution. Infinitely configurable, Production Central leverages your existing [and future] job structure(s) to automatically generate and manage proofHQ proofs and send email notifications.